IDM365 identity and access management for the RBAC/ABAC Hybrid Solution
There are many versions of IAM/IDM solutions on the market that vary in areas like functionality, scalability and ease of use. One of the most important differences is the access control model they use for the systems they are connected to: the traditional RBAC approach (Role Based Access Control) or some version of ABAC (Attribute Based Access Control). By many, including Gartner, ABAC is now being considered as the dominant mechanism for the future. However, RBAC would not have been the standard approach for so long without some merits, so the question should not be as simple as choosing the one over the other.
Features of RBAC
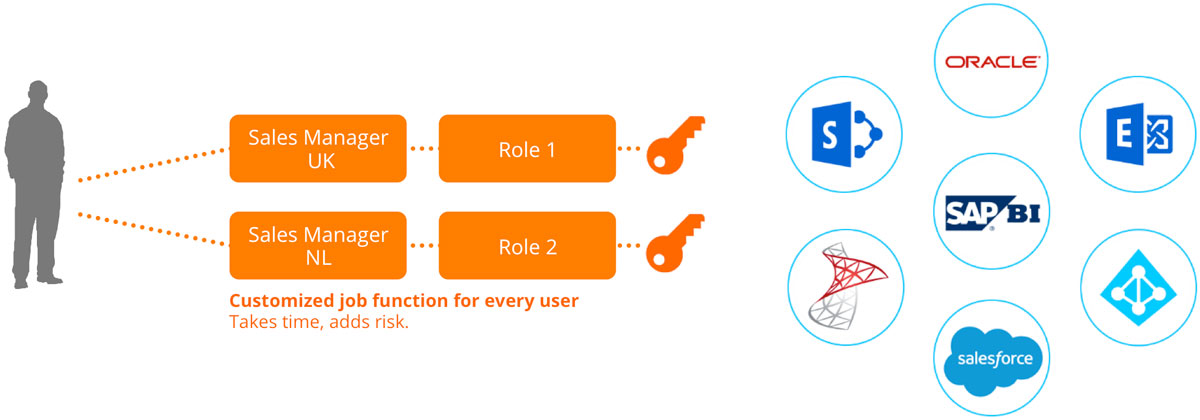
As can be seen accross most traditional systems like AD and SAP, Role Based Access Control (RBAC) is the most natural form of access distribution in an identity management system. The advantage of the RBAC philosophy is that it creates a natural flow in the business for providing access to ‘groups’ of users with similar roles. IAM systems that follow the RBAC paradigm allow users to gain access to multiple systems simultaneously based on predefined roles tailored to their job responsibilities.
The primary benefits of RBAC:
- Rules are simple to set up and distribute
- It is easy to determine who has access to what at any given time (though it can become tedious as the user base grows)
- Rules are static, direct and easy to visualize, allowing security admins to directly see the users and resources that they will affect when creating or modifying a policy
- The system is inherently auditable, as it is simple for business owners to certify or attest to access granted with role based assignments as the consequences of that access can be seen directly
RBAC
Features of ABAC
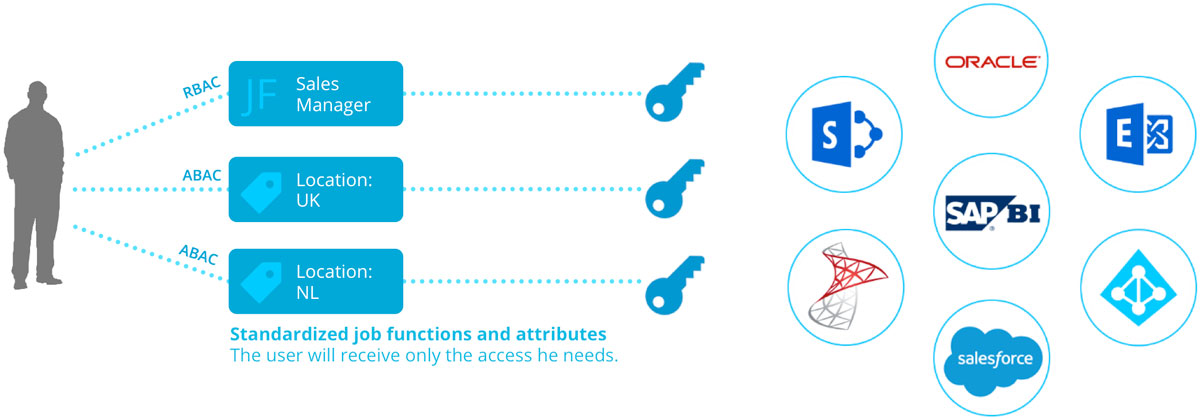
Attribute Based Access Control (ABAC) provides access to users based on who they are rather than what they do: for example, the building they work in and how they were hired. Attributes allow for an easier control structure because permissions can be based on the user’s type, location, department and so on, mirroring the physical aspects of the business. By looking at a user’s attributes—information that is already known and often stored in an HR system—ABAC permits you to express a rich, complex access control policy more simply. For example, if a user named Markus Splaine is promoted from the R&D department to management, his access permissions will be updated because his business attributes changed, not because someone remembered that he had admin permissions and took the time to update a configuration file somewhere.
The benefits of ABAC are many and there are some requirements that can only be achieved using an ABAC model. The most significant benefit is ABAC’s user-intuitive nature that hides technical permission sets behind easy-to-understand user profiles that anyone with authority can update, knowing that the user will have the access they need as long as their attributes are up to date. The other benefit of ABAC is the flexibility it gives; almost anything about the user and the business can be represented, allowing the business to think the business way, not the IT way.
The primary benefits of ABAC:
- Access can be provided automatically without having to make requests or look through existing groups to find one that provides the correct access
- It is easy to specify access rules through simple queries
- Rules can be extremely fine-grained and contextual
- Rules require less maintenance and overhead than RBAC since a separate structure for roles and functions is not needed
- The structure for controlling access is based on the physical aspects of the business
The RBAC/ABAC Hybrid Solution
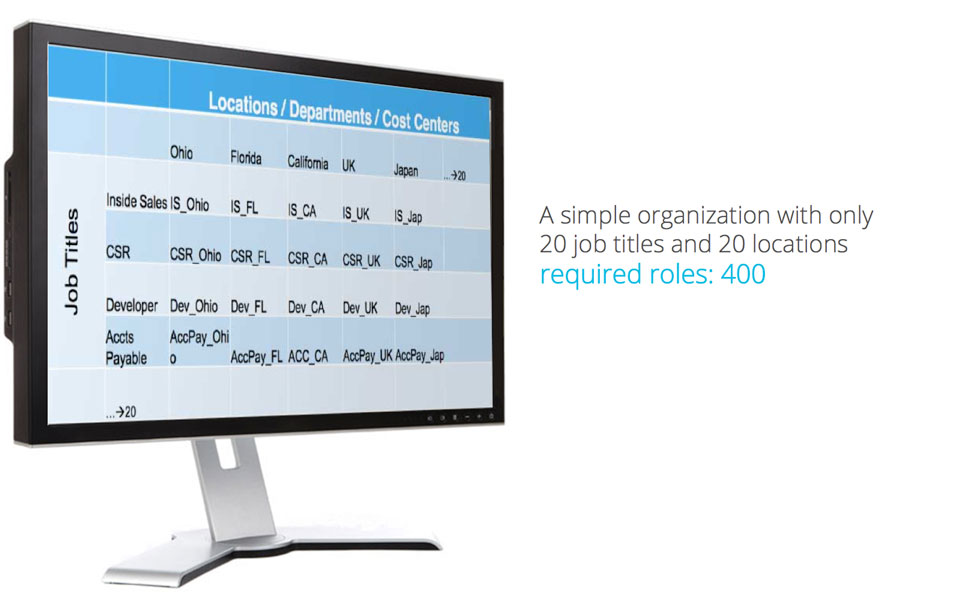
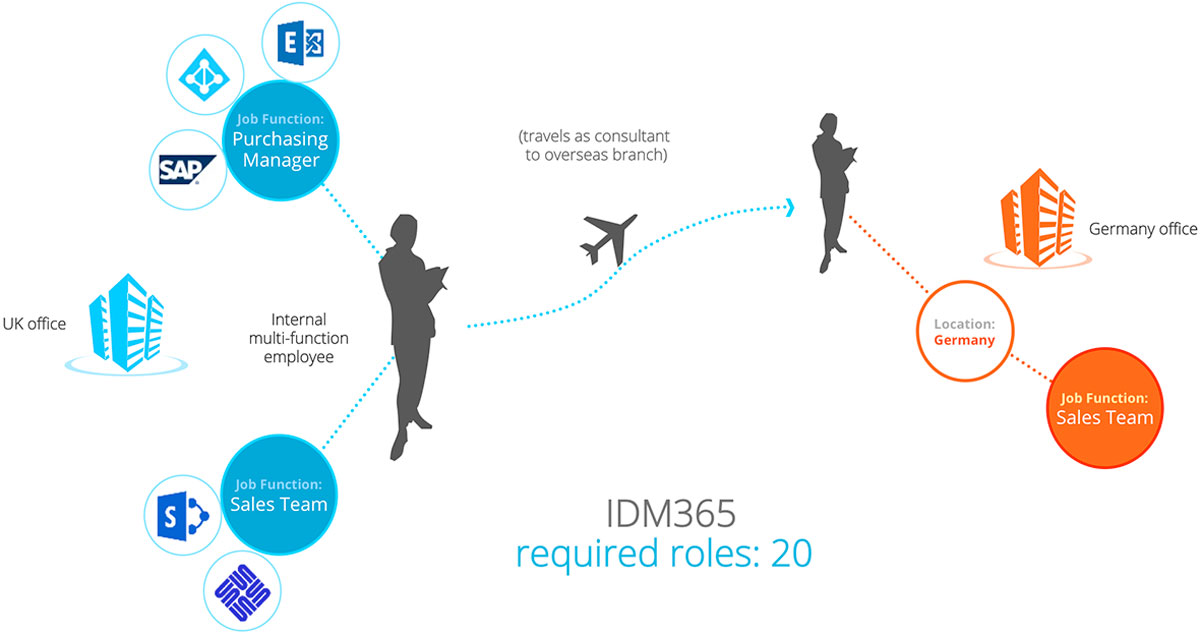
Bridging the gap between RBAC and ABAC is IDM365—a future-ready identity and access management solution capable of designing and enforcing rules based on individual profiles and business environment parameters. IDM365 enforces mandatory access control based on certain attributes while still providing discretionary access control through supercharged roles known as ‘job functions’ that are profiled based on user employment types. To provide risk-adaptable access control, access permissions can be made mutually exclusive through rules pertaining to segregation of duties. Finally, IDM365 provides an attribute store that can act as a repository and attribute exchange platform for the various business and personal attributes attached to each user.
RBAC / ABAC Hybrid
A hybrid approach following both RBAC and ABAC allows the IAM system to combine the IT and Business structures together. While basic access is provided automatically, the business can still provide additional access to specific users through roles that fit into the business structure. By making roles attribute-dependent, additional limitations can be put in place for certain users automatically without any additional searching or configurations, better organizing and reducing the number of access profiles that need to be kept track of. In a larger company with several business units and multifunctional employees, allowing access to be driven by attributes simplifies the process of determining correct access for users. In short, a hybrid structure makes decision-making easier for the business side of things when it comes to assigning user account access to workers. When the approach is combined with a matching user-centric control interface like IDM365, IT is finally able to outsource the workload of onboarding and offboarding users to the decision makers in the business.
The primary benefits of a hybrid RBAC/ABAC solution
- The directory store (e.g. AD) is kept clean
- It is easy access to the right resources to handle specific job functions
- With the right tools, user provisioning can in large part be handled directly by business decision makers, saving IT the hassle
- Rolling out and decommissioning systems can be sped up and handled with fewer personnel, reducing cost
- Access control procedures are standardized
- Risk is reduced through automation and standard audit trails
It is expected that, as time goes on, ABAC will become widely accepted as the authorization model of choice for businesses. A solution which can bridge the gap between RBAC and ABAC is therefore important—an indispensable, high-value software asset for a business-minded future!