IDM:Organize – The IDM365 Identity and Access Organization Tool
The Organize process is step 3 in our four step rapid IAM implementation process, but it can also be performed separately.
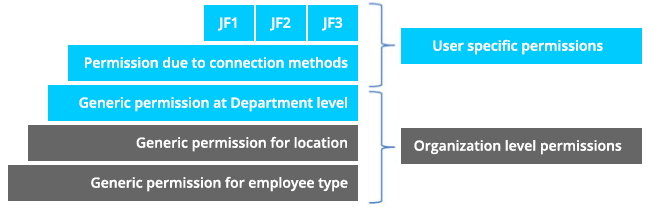
All access permissions and operations that a user needs access to are generally based on two things: their position in the company, and the roles they have been assigned. These two concepts are known as Attribute and Role Based Access Control (ABAC and RBAC). These requirements can also be called job functions. A user may be assigned to handle many job functions based on either the user’s attributes or the roles they need to perform.
Using this model, user memberships can be established or revoked easily as job requirements dictate. New job functions can be established when operations are instituted, and old ones can be removed as operations change and evolve. This simplifies the administration and management of permissions by defining them via job functions, rather than having to update users on an individual basis.
Organizing users into business specific attributes and roles, or job functions, can be a huge and time-consuming task. Maintaining them in an efficient and well-documented manner can be just as hard. The initial process mainly consists of identifying the users’ attributes within the organization’s business units, departments and locations, and then identifying their roles and how they should be adjusted based on those attributes, creating job functions based on the results.
The one handling this process must be able to identify and segment out the full set of permissions required for each user. The results will then enable the business to handle new users in a far more controlled environment, strictly and based on a need-to-know policy that is enforced through identity and access governance.
The Organize Report
The IDM:Organize tool is used to automatically generate suggestions for role design and mapping based on the output from our IDM:Clean tool. The IDM:Organize tool includes a special software engine developed by IDM Scandinavia ApS based on highly complex pattern recognition formulas. It uses the information gathered from existing systems to gather a complete picture of each user including things like their relationship to the company (internal or external), their employment type (employee, temp agent, contractor, etc.), the location where they work and the department they work in.
Based on the identity and access organization analysis, it becomes much easier to group, organize and govern identities and access within your organization.