Build a business layer behind your SAP HCM
IDM365 helps you take full advantage of your SAP HCM cloud or on-premise solution by integrating fully with the infrastructure and handling identity, attribute and rule propagation to not only SAP, but all the systems it has access to. With the IDM365 Identity and Access Management (IAM) solution, you can take full control of your business.
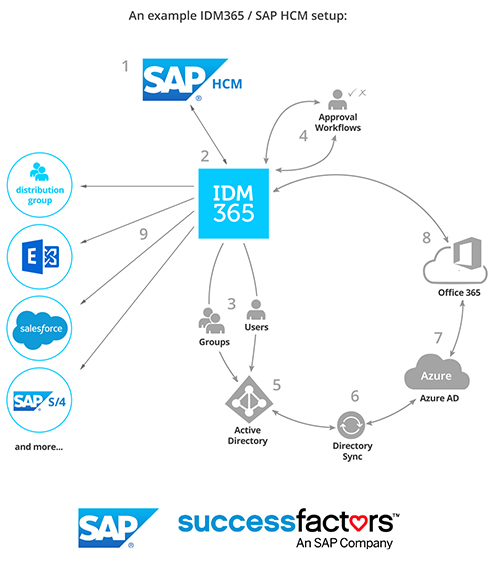
How it works
IDM365 provides a business layer that works alongside your SAP HCM solution. Simply add your workers and their attributes in SAP HCM, and then manage their accounts, keep them up to date, and control their access using IDM365. Synchronization can be set up on one side or both. Either way, IDM365 allows you to maintain workflows, approval requirements, SoD rules, ABAC/RBAC business rules, reports and much more across all your systems centrally with a non-technical interface.
- Get up and running with a self-service portal from IDM365
- Utilize the Sync engine of IDM365 to control provisioning from your SAP HCM system. (Connector from IDM365 to SAP HCM comes out-of- the-box)
- Easily manage the company infrastructure from SAP HCM and control all SoD rules, workflows and reports from within IDM365
Easy Provisioning
Regardless of SSO integration, proper security can only be maintained by making sure that user data and access permissions are kept current in all the systems those users have access to. Where SAP HCM is being used, it becomes an important link in this chain. With IDM365, we believe integrating with Microsoft Identity Manager’s backend provisioning engine is a great way to keep all systems updated. IDM365 on a server with MIM comes with more than 2500 connectors that can be configured for a wide variety of both local and cloud systems. On top of that, it allows full integration with Microsoft Azure which has been SOC 2 and CSA CCM certified.
Our state-of-the-art software has a proven enterprise track record with testing being done on up to 300000 fully managed users. We believe that IDM365 will save you a great amount of time and money while making your organization much more efficient and secure.
 Through integration with IDM365, you can enhance your SAP HCM with a focused business tool that enables your total control. With the added benefits of this hybrid solution, the organization can trust that you have done everything needed to secure it.
Through integration with IDM365, you can enhance your SAP HCM with a focused business tool that enables your total control. With the added benefits of this hybrid solution, the organization can trust that you have done everything needed to secure it.
IDM365 developed its integration with SAP HCM in collaboration with experts in SAP deployment to ensure that your business can take full advantage of all the functionalities HCM has to offer. With MIM’s further integration with Azure, the possibilities with IDM365 and SAP HCM are endless. Whether your solution is onpremise, in the cloud, or hosted in some way, IDM365 will make it work.

Gain Control & Overview
Propagating company data from SAP HCM throughout your whole infrastructure can be demanding, tedious and difficult to automate. Making changes that need to be spread securely to all systems without errors generally requires the assistance of an SAP professional. SAP HCM integration with IDM365 puts business back in control by making these features accessible to non-technical users through an easy-to-use interface. Make the change in HCM and allow IDM365 to align the rest. Sit back and enjoy:
Complete and immediate removal of all access across all resources when a user is terminated, done with the push of a button
Reliable audit logs produced automatically for all access requests, authorization decisions and administrative changes
Tighter security and sustained compliance management via detailed reporting and secure audit capabilities
Centralized security policies enforced across all users and systems
Who has access to what information can be determined immediately
Centralized identification and authorization for all applications
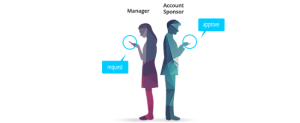
Approval workflows integrated to ensure proper tracking and fulfillment
Adherence to the approval process can be measured in just three clicks
Access management handled through automated processes for the entire user life cycle

Challenge of cost reduction and optimization
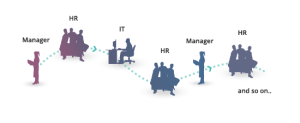
Tedious manual operations
Forms are often manually filled out and sent out, requiring stamped approval by one or more managers. IT personnel who are tasked with managing users must then carry out each request one-by-one in each system and application.
Thousands of hours are usually spent by IT departments carrying out these tasks. It’s not an interesting job but highly paid employees usually carry it out.
On-boarding and off-boarding slows operations
Businesses often suffer because new employees have to wait long periods for their access to get added or updated. Automated role-based access provisioning cuts this time down.
System deployment is complex and resource intensive
Introducing new or upgraded systems can take months of focused work, requiring lots of manual and costly labor to get running fully. Having to make sure
that every user has the correct level of access can be overwhelming and a barrier to upgrading equipment. This can be sped up with a global overview which allow the rapid and secure deployment of such systems.
Optimizing with IDM365
Speed up system deployment
IDM365 provides a structure for managing users that will mirror your business. With a proper overview and means to create access profiles that target users within groups, new systems can be deployed more rapidly than.
Some of IDM365 resource-saving features are:
- Self-service administration and personalization including password resets
- Increased speed and productivity through automation
- Delegated administration that allows data owners to manage access to resources rather than handing it off to a service desk or IT
- Role-based provisioning allowing management to assign new job functions themselves with as little as 3 clicks
Compliance through IDM365
Identity and Access Management (IAM)
It provides a foundation for information security and a top-level way for users to interact with security software and comply with data policies and governances such as the Sarbanes-Oxley Act of 2002 (SOX).
Ensure transparency of complex IT systems
IDM365 provides automated processes for attestation, reporting, and segregation of duties (SoD), enabling your company to enforce policies. Transparency is further augmented by instant, up-to-date documentation and reports covering user access rights and entitlements. With access to all systems, effective governance, risk management and compliance can be achieved.
Enforce access policies
IDM365 provides a strong defense against inappropriate information access through IAM. Rapid, secure processes ensure detailed recording of changes and transactions.
Manage access through roles and attributes
IDM365 merges Role Based and Attribute Based Access Control (RBAC & ABAC) to handle user access in a way that management can understand and that looks at each user individually. As an example, two identical users may require different access if they’re at different locations.
The IDM365 Rapid Implementation Policy
The deployment of a tool for IAM can be tedious and for many often runs over time and over budget. We have developed proprietary tools that allow us to rapidly set up IDM365 in a new environment.
IDM:CLEAN is our analysis tool which we use to generate reports for each system involved in the implementation. These reports identify permissions that are redundant, no longer in use, or that can be removed for other reasons.
Read more about IDM: Clean here
IDM:ORGANIZE is a tool for automatically generating suggestions for role design and mapping based on the data gathered during the CLEAN process. This special software engine was developed in-house based on highly complex pattern recognition formulas.
Read more about IDM: Organize here
These tools will ensure that the implementation of IDM365 stays within the agreed time and scope and adds a transparency so you are on top of the whole project.